Check and
Enable Monitor Mode Packet Injection in Kali Linux, one of the most important question
while we step into the wifi hacking section in our Ethical Hacking career is
just about if a certain Wifi adapter is compatible with the Aircrack-ng tool which
tells that the chipset card which is there in our wifi adapter is capable of
going into monitor mode and allow us to perform packet injection-based attacks.
This is a common
the question that we people usually ask is “I have this wireless card model, can
you tell me whether it is compatible with Kali Linux and can go into monitor
mode packet Injection?” or “Which is the best card that I should buy?” or “Can
my wireless chipset card perform injection based sniffing attacks?” and so on. So,
this tutorial is based on Check and Enable Monitor Mode Packet Injection in
Kali Linux so that no one has any question related to it any further after
reading this article.
How to
enable and operate monitor mode along with packet injection is the most common
discussion in every hackers or beginner in this field. Usb Wifi adapters that are
capable of going into monitor mode packet injection is the most important
the function of any wifi adapter or the wifi chipset rather which makes the attacker or any learner in the field of ethical hacking to be successful in
Wifi hacking subfield.
Monitor Mode
and Packet Injection allows to intercept the targets mac address, find the no
of the possibility of connections and manipulate the network or the server in order
to attack and gain control over it. The most prevalent or the most common example
is a deauthentication attack which comes from the attacker who is not connected
to the network. Monitoring mode is one such mode amongst six different modes a
Wifi card can be enabled for and can be operated which allows the attacker to
capture network packets without having any connection with the access point.
What is Monitor Mode?
Monitor
the mode also is known as
RFMON (Radio Frequency Monitor) mode, allows any computer with a connected wireless
network interface controller (WNIC) or simply a wifi adapter to monitor ever
a single bit of traffic that can be received on the wireless channel which solely
depends upon the range and strength of the wifi adapter. Monitor Mode allows data
packets which are being sent by the router or the host to be captured without
having to connect or paired with the access point network first. Monitor mode
goes into Mon interface with is the short form of Monitor and can only be
applied to wireless networks.
Uses of Monitor Mode include geographical data packet analysis, observation of the widespread traffic which is within its range and acquiring knowledge of Wi-Fi technology used. Monitor Mode is especially useful for auditing unsecured wifi networks. Monitor Mode can also be used to help design Wi-Fi networks.
Limitations of Monitor Mode is that usually that every wireless card doesn't support monitor mode so it was unable to go into Monitor Mode and so is confined to a single wireless network, features and versions of the chipset play the most important role in this section. Also, when the adapter is in monitor mode it does not check to see whether the cyclic redundancy check (CRC) values are correct for packets that have been captured by it, so it may also be like that the captured data packet we want to receive or intercept are corrupted.
What is Packet Injection?
Packet
injection is also
known as spoofing packets, forging packets. Packet injection in networking is commonly
referred to as the process of interfering or changing with a well-established
network or server connection. This is done by means of packets, these packets
appear as a part of a normally connected stream of the network. Packet Injection
process allows unknown third party sources to intercept and capture the network
data packets from the network without connecting. This also leads to the blocking
of the user's permissions to utilize certain mentioned network service protocols.
Packet Injection is commonly used in MITM attacks and DOS and DDOS attacks.
Usages of Packet Injection is disrupting certain services such as file sharing or HTTP by Internet service providers and can also be done the same on different wireless access points. Packet injection also compromises access points and their security. More examples of packet injection are that we can exploit different functions in online games as well as we can also do testing of network firewalls and detect affected systems.
Limitations of Packet Injection, when we run a packet analyzer or packet sniffer on either network’s access points while we try to establish our communication, the result that we get can be evaluated. Usually, during Packet Injection TCP protocol resets are sent to both the access points as well as to the sniffer or the injected network.
Monitor Mode Packet Injection – Why Important?
Monitor
Mode Packet Injection is important because generally, people use Kali Linux or any penetration testing
distribution using Virtualization software such as virtual box and Vmware.
However, this virtualization software fails to detect the internal wifi chipset
which is in our host machine.
Also, if our
the internal card is able to get connected, it is not that strong and capable that
it can be used in ethical hacking purposes and so we need a necessary WiFi
the chipset which supports =Monitor Mode and packet injection as well.
Monitor Mode Packet Injection - Used For?
Monitor
Mode Packet Injection is used for Wifi hacking and securing purposes. This is a type of
feature that is required in wifi chipsets or wifi adapters in order to
penetrate a system. Also without monitor mode packet injection wifi hacking is
not possible and so we cannot perform or secure our systems by performing
security audits.
Commands Used to Check and Enable Monitor Mode Packet Injection in Kali Linux
Before we Check
Monitor Mode Packet Injection it is very important to know what are the
commands that we are going to use in order to finish and execute the process
successfully. So, below are the commands that we are going to use in a serial
order.
ifconfig wlan0 down This command is used for disabling
the Managed mode that is the default mode that any wifi adapter or chipset used
on.
Fairmont-ng check kills This command is used to kill any of the ongoing processes which could
interfere and hamper us while we use our interface in monitor mode. After we enter
this command in our terminal window, our internet connection (i.e. the wifi
connecting option) will be dead until we are in the process.
iwconfig wlan0 mode
monitor This command is used to enabling monitor mode on our
Kali Linux machine.
ifconfig wlan0 up This command is used to enable the monitor mode interface or the MON
interface for us.
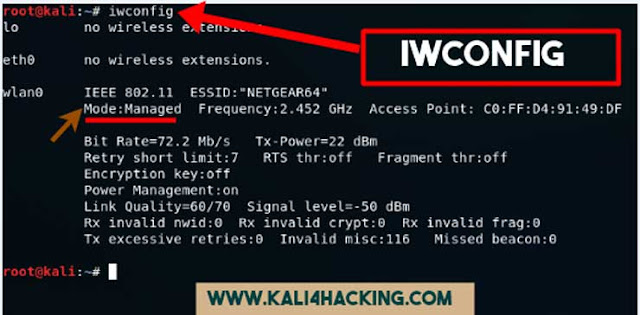
iwconfig This command can be used to
confirm that we are into the monitor mode by just checking our status in the
mode option which will be displayed as the monitor.
How to Check Monitor Mode Packet Injection
So, finally
we are into the main section of the article on how to check and enable monitor
mode and check packet injection.
First use iwconfig to
see the wireless interface
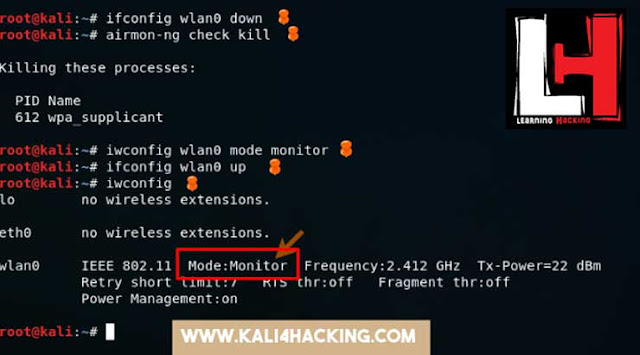
Secondly, use
ifconfig wlan0 down
Now use airmon-ng
check kill
Now to enter
into monitor mode type iwconfig wlan0 mode monitor
Now to
switch on your wifi you just need to turn it on using ifconfig wlan0 up
Best Wifi Adapters that Support Monitor Mode Packet Injection
Everyone
once or most of the time goes on looking to buy an external Wifi chipset which
is capable of packet injection using the Aircrack-NG suite. This practice of
asking has become very uncommon now because now people can have a look at the
following list with supported Wifi adapters which are released and updated by
aircrack-ng official website here.
Also
do check out our article on the top 5 best wifi adapter for ethical hacking and
wifi hacking purposes.
 Thank You for visiting our website
Thank You for visiting our website 




No comments:
Post a Comment